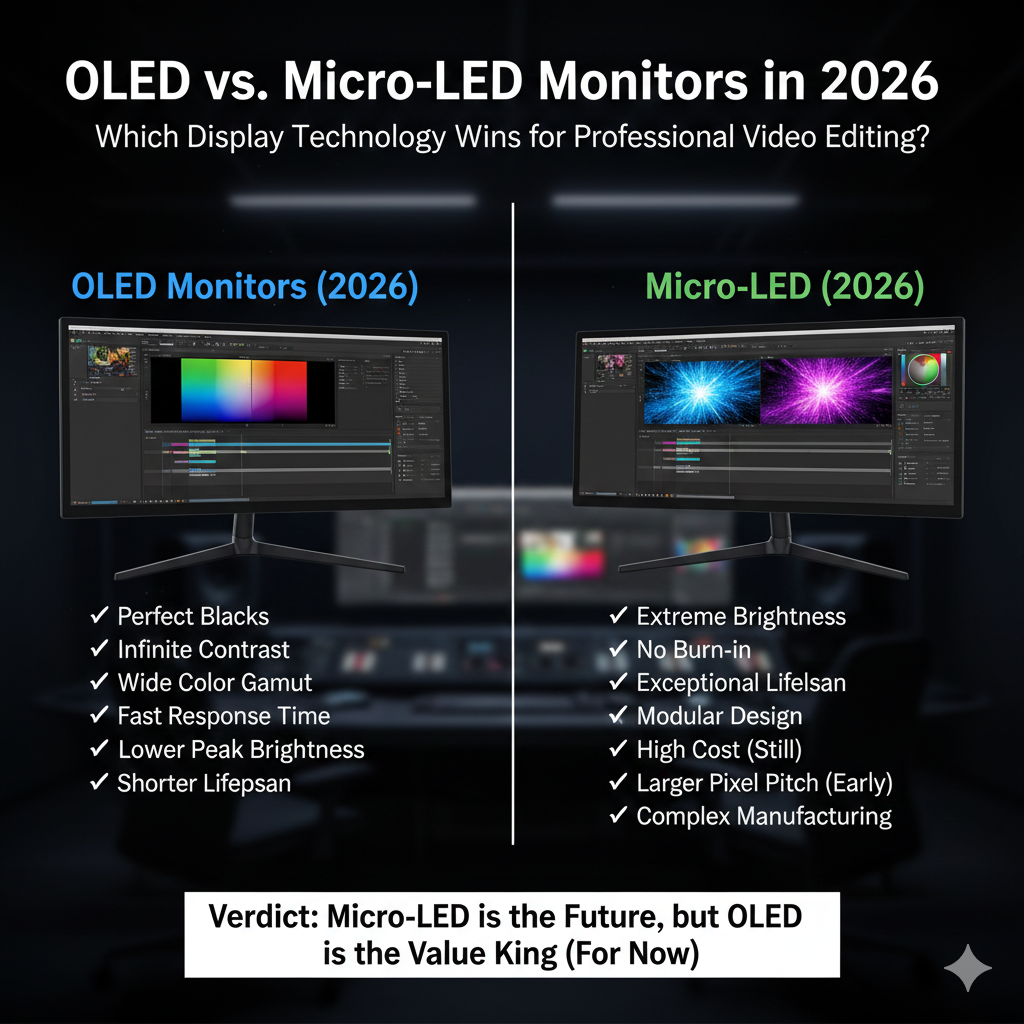
OLED vs. Micro-LED Monitors in 2026: Which Display Technology Wins for Professional Video Editing?
Two cutting-edge display technologies that are now dominating the debate among experts working in video editing are organic light-emitting diode (OLED) and micro-LED. Although they both produce outstanding picture quality, deep contrast, and broad color gamuts, the methods by which they accomplish these attributes are fundamentally distinct from one another. Organic light-emitting diodes (OLED) are used in OLED displays. These diodes enable each pixel to produce its own light, which results in outstanding contrast ratios and perfect blacks. The micro-LED, on the other hand, makes use of inorganic LEDs that are minuscule in size and also self-illuminate. However, the micro-LED has the potential to be brighter and last longer. In the year 2026, both technologies have seen substantial development in comparison to a few years ago; nonetheless, they continue to include different trade-offs that are of major significance in professional workflows. The decision between organic light-emitting diode (OLED) and micro-LED (Micro-LED) displays may have a significant impact not only on the quality of the picture, but also on practical considerations such as the danger of burn-in, the stability of calibration, and the total cost of ownership for video editors who value color accuracy, constant panel performance, and dependability under extended workloads.
How OLEDs Operate and the Benefits They Offer
By sending current through organic compounds that generate light separately at the pixel level, organic light-emitting diode (OLED) monitors are able to display pictures. Real blacks and nearly limitless contrast are made possible as a result of this feature, which allows pixels to be turned off entirely. For those who edit videos, this implies that shadows and highlights will seem more subtle and faithful to the reference material that is taken from the actual world. Generally speaking, the color saturation and viewing angles are outstanding, which is an essential quality to have when grading film. In addition, contemporary OLED panels are capable of supporting vast color spaces like as DCI-P3 and Rec.2020, which guarantees that they are in accordance with professional standards. The versatility of OLED design also makes it possible to create screens that are smaller and lighter, which is desirable in studio settings where space and ergonomic alignment are important considerations.
Fundamentals of Micro-LED Arrays and Their Benefits
An example of a more recent generation of self-emitting display technology is the micro-LED, which employs very small inorganic LEDs for each individual pixel or cluster of pixels. Unlike organic light-emitting diode (OLED), micro-LED does not depend on organic components. As a consequence, it has the ability to achieve greater levels of brightness and has a longer lifespan. These properties are especially useful in situations for video editing, which demand steady performance over extended periods of time and low deterioration over the course of time. As a result of its ability to attain exceptionally high peak brightness without the danger of burn-in, micro-LED displays are perfect for processing high dynamic range (HDR) material, which is when luminance performance is of the utmost importance. As a result of the technology’s ability to generate vast color gamuts and good uniformity across big screens, it offers professionals visuals that are both stable and predictable.
HDR performance, contrast, and black levels are all important.
It is impossible to deny that OLED has an evident edge in terms of contrast and black level reproduction due to its per-pixel light management. This functionality enables editors to view every detail in situations that have deep shadows or delicate gradient transitions without the halo distortions that are often visible in backlit LCDs. In addition, HDR editing is able to take use of these properties, especially in gloomy situations where OLED can preserve information without causing the blacks to become crushed. In many implementations, micro-LED still depends on pixel clusters or zones for local dimming, which might restrict fine-grained control in comparison to genuine pixel-level dimming. Despite the fact that micro-LED is capable of high brightness and superb color, it still relies on these methods. The much increased brightness capability of Micro-LED, on the other hand, has the potential to make HDR highlights look more powerful and closer to the luminance levels that are seen in the real world.
Accuracy of Color and Calibration Over the Course of Time
Micro-LED panels and organic light-emitting diode (OLED) panels are both designed to enable professional calibration tools and color profiles in the year 2026; however, they vary in the manner in which they maintain their accuracy over time. Due to the aging of organic material, organic light-emitting diode (OLED) displays may undergo modest changes in color performance and brightness after extensive usage. The effects of this impact are often gradual and may be managed by frequent calibration; nonetheless, studios that rely on long-term stability must still take this into consideration. Because inorganic LEDs are more stable during their lifetime, micro-LED panels are often better at maintaining calibration. This is because inorganic LEDs reduce drift and the need for frequent recalibration due to their increased stability. In contexts with a large volume of editing, where consistent output is required, this consistency may transfer into performance that is more predictable.
Long-Term Reliability and the possibility of burn-in
The possibility of burn-in, which occurs when static interface elements might leave ghost images on the screen after prolonged exposure, is one of the characteristics of OLED technology that has generated the greatest scrutiny and discussion. In the year 2026, contemporary OLED displays have included mitigating strategies such as pixel shifting, automated dimming of static logos, and intelligent panel management; yet, the danger has not been completely eradicated. This may be a valid worry for editors who keep user interface elements in a static state for extended periods of time. On the other hand, micro-LED displays do not include any organic components, and as a result, they do not experience burn-in. This makes them an excellent choice for extensive use with static information such as timelines, scopes, and user interface overlays. When it comes to experts that put in long hours every day, this dependability may be sufficient to justify the increased pricing.
Controlling the Brightness and the Ambient Light with
Lightness is yet another domain in which these technologies differ from one another. The peak brightness levels of OLED displays are usually lower than those of Micro-LED displays, which are able to attain far higher nit values without affecting the health of the panel on which they are shown. It is easier to retain picture clarity and contrast when using Micro-LEDs because of their increased brightness, which is beneficial in bright studio situations or spaces with substantial ambient light. This is especially helpful when evaluating video in high dynamic range (HDR) or when working with customers in conditions where there is enough lighting. Additionally, OLED displays continue to operate magnificently and provide good visual clarity even in dimly illuminated environments; nevertheless, the somewhat lower peak brightness of OLED displays might be a limiting issue in certain professional processes.
Price, Availability, and Considerations From a Practical Perspective
OLED and Micro-LED displays both have premium price tags in the year 2026; nevertheless, Micro-LED monitors continue to be much more costly than OLED monitors owing to the complexity of their production process and their lower yields. In recent years, OLED displays have become more widely available in a variety of sizes, catering to both professional studios and casual consumers. The accessibility of large-size format In spite of the growing demand, the availability of micro-LED screens is still restricted. By providing the best compromise between professional-grade picture quality and cost, an OLED panel may be the greatest option for video editors who are trying to strike a balance between performance and price. In situations where finances are available and when the technological benefits of micro-LED directly assist processes that are mission-critical, it is attractive for top-tier studios to use this technology.
Tips for Selecting the Appropriate Display for Video Editing
Your particular workflow and goals are ultimately the most important factors to consider when choosing between OLED and Micro-LED for professional video editing. Optical light-emitting diode (OLED) displays continue to be an excellent option for those who want extensive color coverage, deep black levels, and immersive contrast in a more cost-effective form. Because of its capacity to produce visually attractive results while still accurately reproducing color, it is an excellent choice for a broad variety of editing chores. Micro-LED displays, on the other hand, are the future of high-end professional displays. If your job requires the maximum possible brightness, long-term calibration stability, and zero chance of burn-in, then Micro-LED displays are the way to go. Even if both technologies have reached a significant level of maturity by the year 2026, they continue to fulfill somewhat distinct requirements within the ecosystem of video creation. When you make a sensible choice, you connect your tools with the way you operate on a daily basis and choose which parts of image fidelity are most important to you because of your creative process.